
Vertali’s zTrust is a unique software solution that dramatically reduces the time, effort and costs needed to secure your operations and prove compliance with data standards and industry regulations.
zTrust reveals network activity to and from your mainframe, confirming that your network access controls are correct—and ensures access for authorized users only while denying everyone else.
While mainframe sites can have a reasonable view of who is using applications at the userid level, most don’t have an accurate, up-to-date picture of actual network activity. And that can quickly become a problem in today’s heightened threat landscape.
“Ensuring your network security policies are correct and are being regularly updated is critical,” says Tony Amies, Software Technical Director, Vertali. “The most important step is network discovery: gaining a full and accurate understanding of your network resources, connections and traffic patterns, so you can set the right policies and better protect your systems, data and people.”
You need to know precisely who and what are accessing your network at all times and compile a constantly evolving network knowledge base. That hasn’t been easy—until now.
zTrust for Networks means you can understand and protect your network like never before to improve cybersecurity and ensure compliance.
zTrust Reduces Time, Effort and Risk
This unique software, tested and proven by a global bank, is now available worldwide to dramatically reduce the time, effort and costs involved in detecting, monitoring and enforcing network access. Differentiating between clear and encrypted network connections is the key.
zTrust detects, identifies and provides alerts covering:
- Applications permanently or temporarily accepting inbound nonencrypted and/or inbound encrypted connections
- Applications making outbound non encrypted and/or outbound encrypted connections
- Network segments accessing specific applications without encryption and/or with encryption
A notable use case is helping you to adhere to data compliance standards and regulations including PCI DSS (Payment Card Industry Data Security Standard), HIPAA (Health Insurance Portability and Accountability Act) Privacy Rule, GDPR (General Data Protection Regulation), CCPA (California Consumer Privacy Act) and the Sarbanes-Oxley Act (SOA).
Why You Need zTrust
In a growing threat landscape, we need to understand from where users are coming, any attempted but rejected connections to applications, attempted connections to closed ports, outbound connection activity, UDP activity, IPv6 activity and more. zTrust enables that.
For most organizations, it’s rare to have easy access to up-to-date and accurate information on which network devices or segments are connecting to specific applications, and whether they are correctly encrypted. Most security mechanisms focus on incoming IPv4 TCP connections but few look at controlling outbound connections too.
Unfortunately, any user can initiate an outbound connection to a remote and possibly insecure system, with hackers using outbound connections as a backdoor to mainframe services.
Network Discovery: Understand and Secure Your Network
TCP/IP was originally intended to allow any-to-any connectivity with minimal configuration. But this conflicts with today’s security policies, aimed at limiting connectivity to only those with proper authorization. While some controls are available in z/OS Communications Server and SAF to limit TCP/IP connectivity, the default for many sites is to allow connections.
The problem: Many of the metrics required to understand connections are not easily available in typical SMF records and, even for the ones that are, the volume of records required on a production system would be unacceptable.
This is where zTrust Network Discovery comes in, enabling a full and accurate analysis of network activity involving the mainframe without relying on high volume SMF processing. Opportunities presented by zTrust Network Discovery include the ability to limit application access to a specific network segment or specific network device—providing an additional layer of security.
Network Micro-Segmentation: Take Control
Micro-segmentation is a way to control network access and better protect your systems and is often required for regulatory compliance such as PCI DSS. In this example, isolating card payment processing applications to specific network segments can significantly reduce the scope, time and cost of compliance reviews.
zTrust is unique in using the Enterprise Security Manager (ESM) such as RACF, ACF2 or TSS to manage network segmentation, moving the responsibility for compliance and standards to the security team—where it should be. Here’s how it works:
- zTrust software uses standard SAF controls and commands to isolate specific parts of the mainframe envrionment at the network level.
- You control access by permitting network segments to access specific applications, rather than blocking or enabling access to the mainframe in its entirety.
- This approach applies additional management, implementation and monitoring controls to systems with different security requirements, reducing the number in scope.
“You focus security policies on only the segments required,” says Mark Wilson, Technical Director, Vertali Ltd. “While it’s possible to do this manually, the time and costs can make it prohibitive for large and complex organizations.”
zTrust for Networks neatly replaces the complexities required to manually create and maintain policy agent access control lists, generating them automatically from access controls defined in the ESM. Further management of micro-segmentation can be performed using standard RACF|ACF2|TSS or fully managed from a Vertali browser-based user interface.
Blocking All Unencrypted Connections
zTrust detects whether connections are encrypted or not, then implements network segmentation based on that.
In other words, defining an SAF permission to allow a network segment to access a specific application but only if the connection is encrypted. All unencrypted connections would be blocked. This approach means you can:
- Avoid the complexities in manually creating and maintaining policy agent access control lists
- Dramatically reduce the time, effort and costs in ensuring and proving compliance
- Benefit from periodic reporting for compliance audits
- Improve cyber resiliency and achieve more secure operations in general
- Move closer toward a zero trust security stance
Tony Amies of Vertali adds, “zTrust is an additional layer of security in front of your applications. It coexists with controls managed by the z/OS ESM such as user access, multifactor authentication (MFA) and encryption—it doesn’t replace them.”
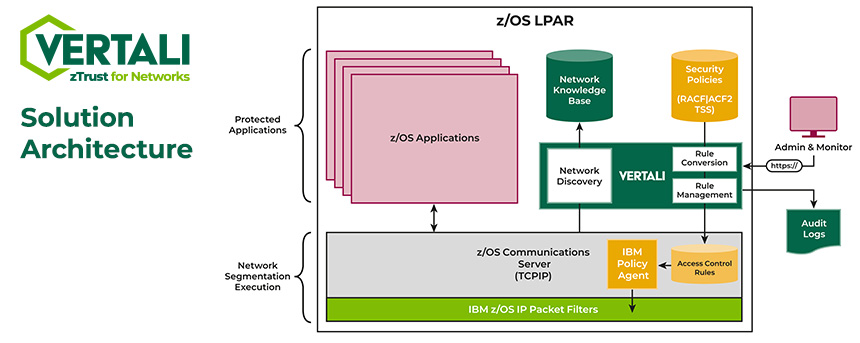
Vertali zTrust enables you to:
- Discover and fully understand your network resources, connections and traffic patterns
- Enforce encryption using ESM rules — block unencrypted traffic
- Create and maintain IBM Policy Agent access control rules
- Manage and monitor your implementation and ensure high performance
- Enable periodic reporting for compliance audits
You benefit from:
- Unique insights via zTrust Network Discovery; build a complete map of network activity
- An innovative way to manage network micro-segmentation using ESM (RACF | ACF2 | TSS)
- The ability to isolate specific aspects of your environment at network not userid level
- Periodic reporting for compliance
- Dramatically reduced time and costs of compliance assessments
Register for the webinar: AI-Driven Insights: Transforming Application Performance Management in a Hybrid IT Environment
Vertali has a long pedigree in providing IBM mainframe skills, resources, and software tools to organizations around the world. The company’s mission is to help its clients to reduce risk, work smarter, and deliver their mainframe strategy.www.vertali.com



