Featured
No Results Found
The page you requested could not be found. Try refining your search, or use the navigation above to locate the post.
No Results Found
The page you requested could not be found. Try refining your search, or use the navigation above to locate the post.
Recently Published

Why Mainframe Observability Matters in Unifying Hybrid IT Operations
Let’s be honest: mainframes are mission-critical but often seen as separate technological islands that can get left out of the observability conversation. Distributed-based, leading observability solutions such as DataDog, Dynatrace, New Relic, Splunk et al. have...

Unlocking Mainframe Talent: Skills, Mentorship, and Hiring Trends ▶️
Mainframe talent is in demand. Broadcom reports that 91% of organizations plan to hire mainframe system administrators or application developers within two years. For IT leaders, the need for skills development, mentorship, and knowledge transfer is urgent. In this...

Building a Global Mainframe Talent Pipeline: Broadcom’s Investment in Customer Success
It may come as a surprise that the narrative of a vast mainframe skills gap is…false. More precisely, it’s outdated.The Futurum Group says that sourcing mainframe skills “is no harder than finding cybersecurity or AI talent.” So, how difficult is it to hire...

The good, the bad and the ugly: generative AI and cybersecurity
Putting the AI into mAInframe security Artificial intelligence can be as much a help as a threat: a powerful tool in the hands of either the good, the bad or the ugly. Today’s threat landscape and cybersecurity requirements are more complex and challenging than ever....
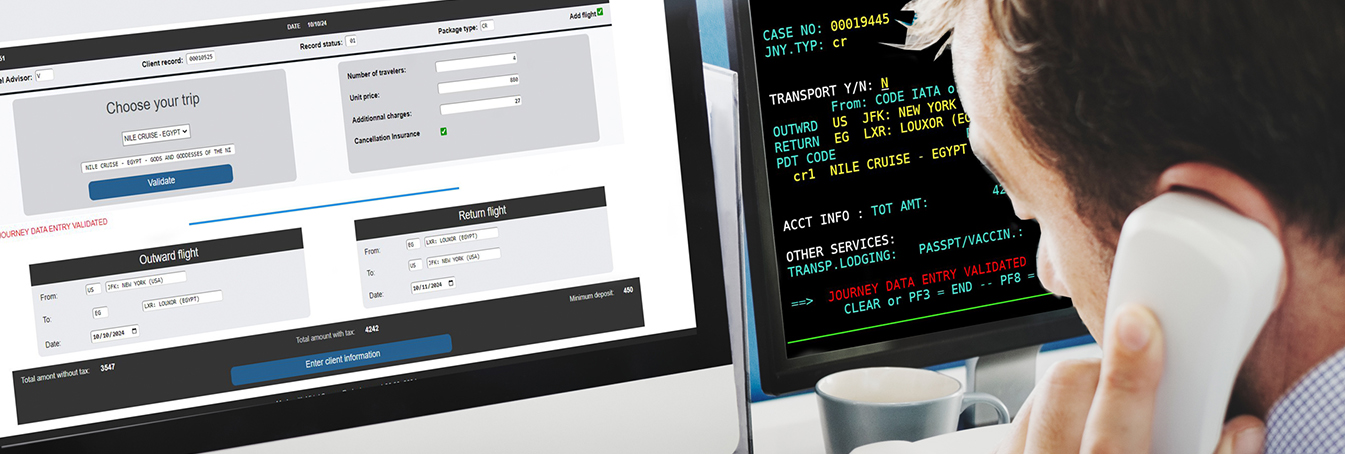
Improving the Mainframe User Experience: A Company’s Journey to a Modern Web Interface
Marsh McLennan’s journey to transform a crucial 3270 application into a modern web interface Modernizing business applications is a critical need for many large enterprises that rely on these powerful legacy systems for their core operations. This blog post...
Mainframe Trailblazers – Part 4
Here at Planet Mainframe, January is the month to focus on talent and training, and this week’s Trivia quiz follows suit with a quiz on some of the big talents that blazed the trail of the mainframe. These innovators have left an indelible mark on mainframe computing,...

OpenTelemetry for End-to-End Hybrid Observability
How CA 7™ Observability with OpenTelemetry Bridges the Mainframe Data Gap for Unified Insights In today’s interconnected world, customer experience hinges on the reliability of the services. When technology fails, customers don’t hesitate to voice their frustrations...

IBM TechXchange, New Podcasts and Presentations, and Semeru Runtime Certified Edition for z/OS
IBM TechXchange Developer Day: Virtual Agents On January 23rd at 11 AM ET, Armand Ruiz, Vice President, Product Management, AI Platform and founder of NoCode.ai will kick off 12 hours of deep technical content to quickly advance your AI journey from...
Sign up to receive the latest mainframe information
Upcoming Events
Events
-
-

Mainframe Virtual User Group: Unlocking the Core—API-Driven Data Access in CICS
Virtual MeetingMainframe data is no longer a "black box." As organizations push for real-time insights and seamless hybrid cloud integration, the ability to access CICS-managed data via modern APIs has become […]
-
Virtual Db2 User Group | March 24, 2026
Zoom - Virtual Meeting -

Essential z/OS Performance Tuning Workshop – Registration Deadline: March 16, 2026.
The 4-day z/OS Performance Tuning Essentials Workshop introduces the foundational terminology, metrics, and practices necessary to measure, understand, and improve z/OS system performance. Participants will gain a comprehensive understanding of […]
-
-
Virtual IMS User Group | April 14, 2026
Zoom - Virtual Meeting

Introducing LinuxONE 5 and trends for 2025
IBM Introduces LinuxONE 5: A Sophisticated Approach to Security, Efficiency, and AI Integration for Modern Enterprises On May 6, 2025, at its annual THINK conference, IBM rolled out the IBM® LinuxONE 5, an advanced computing platform designed with the complexities of...

Influential Mainframers Trivia
April at Planet Mainframe was all about celebrating today’s Influential Mainframers, and if you’re looking for inspiration, the full list of honorees is well worth a look. Today, seeing women’s names among industry leaders might feel expected—but it certainly wasn’t...

AI Innovation, Mainframe Leadership, and Big Moves Ahead: Highlights from IBM Think, Terminal Talk, and Kyndryl’s 2025 Success
IBM Think 2025 in Boston IBM’s annual Think conference will be in Boston this year, and it’s only a couple of weeks away, taking place May 5-8, 2025. Join 5,000+ senior business and technology leaders to gain exclusive insights, breakthrough strategies, and real-world...

Sustainable IT and the Role of Mainframes in a Greener Future
As organizations face increasing pressure to reduce their environmental impact, sustainable IT practices have become a strategic priority. While mainframes have long been known as the workhorse of enterprise computing, quietly powering critical applications behind the...
New PopUp Mainframe Market Survey Lifts Lid on Challenges and Opportunities Ahead
Mainframe enterprise software company PopUp Mainframe has released the initial findings of its 2025 Mainframe Market Survey, which reveals the latest market trends and 2025 plans for enterprises utilizing IBM mainframe technology. The survey reveals the continued...

Wüstenrot Gruppe transforms IT, Precisely expands with a recent acquisition, and more
Precisely expands mainframe offerings through DTS acquisition Precisely is signaling a renewed focus on its mainframe heritage with the acquisition of DTS Software, a company known for its mainframe storage optimization tools. While Precisely has broadened its...



